Outlook Encryption
 |
|
|
|
|
Person To Person now provides full RSA Security for Microsoft Outlook without the need to purchase digital certificates. 
Person To Person makes it easy with a Security Toolbar in Outlook which controls encryption of message body and email attachments. Emails can be encrypted automatically or on a case by case basis. Person To Person guarantees that the only person who can read the email is the person it is addressed to. Outlook encryption of email using Person To Person does NOT require you to purchase digital certificates - a significant cost and security benefit. Use self-decrypting attachments to make it easy for the receiver. No software is required at the other end, they simply click the attachment and it self-decrypts. NEW - "Shred-by-Age" feature allows you to set a time limit (in days) after which the email is effectively shredded. This means there is no risk of your emails lying around unencrypted in Outlook folders (yours and other peoples) and on isp servers for years. 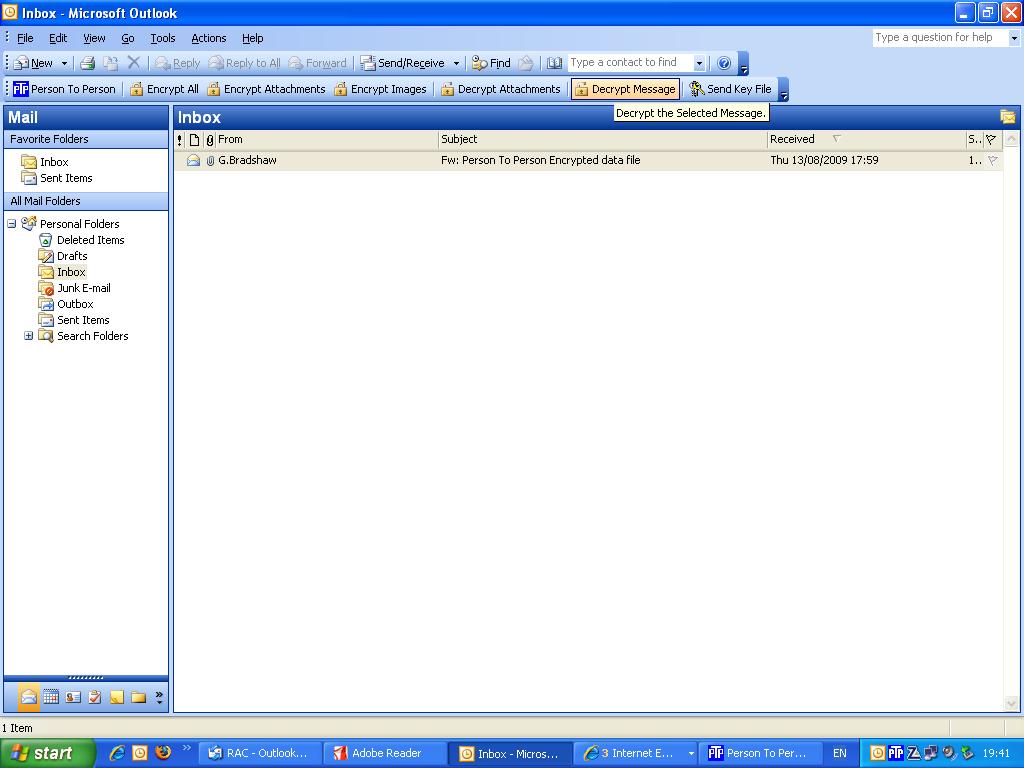
Person To Person Outlook encryption integrates seemlessly with Outlook during the installation procedure when you are asked to choose installation for Outlook 2003, Outlook 2008, Outlook 2010 and Outlook 2013. The installation procedure creates an add-in for Outlook which displays an additional encryption toolbar when Outlook is run. The new toolbar allows Outlook to encrypt emails at the click of a button, or alternatively set Outlook to automatically encrypt/decrypt all emails. Incoming emails are automatically decrypted without the use of a password. Emails stored in Outlook folders can now be secure. The new 'SHRED' feature means that they can only be read for a specific time period, which means that readable emails are not left lying around in folders for years. Free license is not time-limited and provides many useful security features free of charge such as Symmetrical Encryption and Data Signing. With the free edition license you can SIGN & ENCRYPT files for email attachment or for safe keeping on memory sticks. Using Person To Person in OutlookWhen Outlook integration is installed and enabled, you will see a new PTP tool bar below the regular Outlook tool bars. This PTP tool bar, along with a menu on Outlook's Tools Menu, allow you to select the encryption/decryption operations to be performed on email messages. Selecting these options on the main toolbar sets the option for ALL messages. When sending a message, the options will appear on the toolbar of the message compose window preset according to the global options you may have selected. You can then adjust the encryption options only for the message you are composing. You can select from the following options by clicking on the button (highlighted means the option is ON): Encrypt All Encrypt the email message body text and any attachments to the message. The body is replaced by boiler plate text. The encrypted body text is sent as an attachment. Encrypt Attachments Encrypt only the attachments to the message. The body text is left in plain text form. Encrypt Images Encrypt any images embedded or attached to the message. Images are not encrypted by default. Decrypt Body Automatically decrypt the message body on incoming email messages resulting in the message body being in clear text form. If not selected, the message body will remain encrypted, as an attachment to the message. You can click on such an attachment later to invoke the PTP program to decrypt the file on demand. You can also use the Decrypt Message toolbar button (see below) to decrypt the message body attachment. Decrypt Attachments Automatically decrypt attachments with the .PTP extension on incoming email messages resulting in the attachment being in clear text form. If you do not select this option, .PTP files will be left as .PTP (encrypted) files. You can click on such an attachment later to invoke the PTP program to decrypt the file on demand. You can also use the Decrypt Message toolbar button (see below) to decrypt the attachments. You can select from the following operations by clicking on the button: Decrypt Message This button will only appear when the currently selected message in the email client explorer window has attachments with the .PTP extension. Clicking the button will immediately decrypt all the attachments. This is useful if you turn of Decrypt Attachments and so have messages with attachments still encrypted, or, when there are problems decrypting attachments and they are left in the encrypted state. Send Key File This button will send a Public Key File to the currently selected Contact(s) or to the sender of the currently selected email message(s). This option also appears on the Tools pull down menu and on Contact/Message context menus. The message may be sent with the Outlook default email account or you can manually set this on each Public Key File message. See Settings. When a new mail message is sent, or a new message is received, if encryption or decryption operations are required, your email client will start the PTP program and communicate with it to perform the needed operations. You will be required to login if the PTP program is not already running. You will not see the PTP main screen, but you will see progress displays as operations are performed. Once all PTP processing is complete, the new message is either sent when sending a message or placed in the Inbox when receiving a message. When encrypting a message, a PTP Contact must be selected. The email client will submit the message recipient's name and email address to PTP which will attempt to match one of your Contacts with that information. If a Contact is matched, it is selected for the encryption operation. If no Contact is matched, the encryption operation will cannot be performed. In that case you will be shown a warning and given the option to send the message as a Self-Decrypting file (with password), unencrypted or to cancel the message. When a message or attachments are automatically decrypted or have decrypted a message on demand (Decrypt Message button), the decrypted message body text will replace the boiler plate text in the message and attachments will be decrypted but remain as attachments. If you double click an attachment with the .PTP extension, that file will be sent to the PTP program to be decrypted as a normal file into the current working directory of the PTP program. When a Public Key file is decrypted automatically by selecting Decrypt Attachments or you decrypt on demand with the Decrypt Message button, the Public Key file will be processed and the Contact information encoded in it will be added to the PTP Contact List. In these two cases, the email address of the person who sent the Public Key file will also be recorded in the PTP Contact List. If you receive a Public Key file and do not decrypt it with one of the above methods, no decryption action occurs. If you the double click on the Public Key file attachment in Outlook, the Public Key file will be decrypted and the information added to the PTP Contact list, but the sender's email address will not be included. At any time, you may place the cursor over the email address area of a Contact's information line and double click to edit the Contact's email address. When Outlook needs to use PTP to process email encryption, it will check to see if the PTP program is already running on your desktop. if it is not, it will be started. Outlook will wait only so long for the PTP program to start and if it does not start in the allotted time, Outlook will abort the encryption and report an error. You can change the startup timeout on the Settings screen. When messages fail to encrypt, Outlook does not send the message and the message composition window remains open. If decryption fails, the encrypted files are ignored and remain attached to the message. Note that with Outlook, messages that are in RTF (Rich Text Format) have encryption limitations. If a message is in RTF format and has any attachments, no encryption can be done. If the message has no attachments, then the message body can be encrypted. Currently, in Outlook, only Mail Messages are processed by PTP. Appointment, meeting request and task messages are not supported. In Outlook, you may create Contact User Fields to control automatic encryption. This allows you to not enable encryption at the global level (main toolbar) but instead set encryption for individual Contacts in the Outlook Contact list. This means messages to the Contact will be encrypted as you select, automatically, without you having to worry about choosing encryption at the global or new message levels. The User Fields are: PTP Contact Set to name or email address that will be used to look up the encryption Contact in the PTP database. Overrides normal use of Contact email address and then Contact name. PTP Encrypt Contents If Yes, messages to the Contact will be fully encrypted. If No, encryption is controlled by the toolbar options selected on the compose window. PTP Encrypt Attachments If Yes, messages to the Contact will have any attachments encrypted. If No, encryption is controlled by the toolbar options selected on the compose window. PTP Self-Decrypting Password If set, messages to the Contact will use Self- Decrypting files as the encryption scheme using this password. In Outlook there are 3 email addresses available for a Contact. You can define the above User Fields for each of the 3 addresses. For example, PTP Contact associates with email address 1. PTP Contact 2 associates with email address 2 and PTP Contact 3 associates with email address 3. In order for User Fields to be effective, PTP must search your Outlook Contact database for the message recipient's Contact record to see if it has User Fields and if so, determine how they will affect the encryption process. This Contact Lookup can take significant time if your Contact database is large or if you are attached to an Exchange server. If you are not using User Fields, you can disable this lookup process on the Settings screen. In Outlook 2007/2010, on the detailed Contact window, the Ribbon Bar will contain check boxes to set the PTP Encrypt Contents/Attachments fields for you. Just check the appropriate box. In Outlook, if a message to be sent is encrypted, PTP can keep a plain text copy of the encrypted message if you select Attach Original to Encrypted Message in Sent Items on the PTP section of the Tools pull down menu. If this option is selected, a plain text copy of the message to be encrypted is placed in the Sent Items folder. When the encrypted message is sent and moves to Sent Items, PTP will attach the plain text copy to the encrypted message. This provides a readable copy of the encrypted message for your records.
Because Person To Person is based on encryption standards it means that you know exactly what you are getting. It does not use propietary algorithms which have no track record. RSA has had over forty years of rigourous practical testing in the field. All secure internet pages and online credit card transactions rely on RSA being secure. Without RSA being mathematically sound, the commercial internet could not exist. However, very few encryption tools use RSA and most of those that do rely on digital certificates which have their own security weaknesses. Person To Person exceeds the following NIST standards:USA Federal Information Processing Standards FIPS 180-2 USA Federal Information Processing Standards FIPS 140-2 USA Federal Information Processing Standards FIPS 46-3 U.S. National Institute of Standards and Technology (www.nist.gov) FIPS Publications are issued by NIST after approval by the Secretary of Commerce pursuant to Section 5131 of the Information Technology Reform Act of 1996 (Public Law 104-106) and the Federal Information Security Management Act of 2002 (Public Law 107-347). The Computer Security Division (http://csrc.nist.gov) is one of six divisions within NIST's Information Technology Laboratory. The CSD mission is to provide standards and technology to protect information systems against threats to the confidentiality of information, integrity of information and processes, and availability of information and services in order to build trust and confidence in Information Technology (IT) systems.Person To Person exceeds the following ISO standards:ISO 10118-3 ISO 18033-2 ISO 18033-3 ISO (International Organization for Standardization wwww.iso.org) is the world's largest developer and publisher of International Standards. ISO is a network of the national standards institutes of 159 countries, one member per country, with a Central Secretariat in Geneva, Switzerland who co-ordinate the system. |